Article
January 27, 2025
A Guide to Selling a Cyber Security Services and Solutions Business
Unlock maximum value when selling your cybersecurity firm with a future-focused strategy.

Table of Contents
Exiting your cybersecurity services and solutions business may feel like standing at the edge of a fortified castle’s walls, unsure of how to step outside without leaving vulnerability behind. Yet, with the right strategy, timeline, and preparation, you can convert the countless hours spent building threat intelligence systems, penetration testing protocols, and compliance frameworks into a successful exit. By understanding the unique markets, key valuation levers, and strategic buyer expectations, you can properly navigate the delicate process of transferring your cyber security business to a new owner—while maximizing its market value.
Below, we’ll delve into the critical factors that influence how to sell a cybersecurity business, highlight key operational considerations, and provide specific steps to help you secure a profitable exit.
Why Cybersecurity Businesses Are Unique
Essential Services
Cybersecurity services have become mission-critical in a digital-first world, making them a “must-have” for clients of all sizes. Unlike optional discretionary purchases, robust cyber security solutions protect a company’s data, reputation, and bottom line. This ongoing demand acts as a stabilizing force, ensuring a fairly predictable income stream even when broader economic conditions fluctuate.
Recurring Revenue Streams
Many cybersecurity firms build recurring revenue through managed security services (MSS), continuous threat monitoring solutions, and monthly subscription packages. These consistent revenue streams can significantly boost valuation multiples, making your cybersecurity business a more attractive target. Prospective buyers appreciate the predictable cash flow that monthly recurring services, managed threat detection, or incident response retainers can generate.
Regulatory & Licensing Requirements
Navigating frameworks such as NIST, ISO 27001, PCI-DSS, or HIPAA compliance sets high barriers for entry but also protects your competitive advantage. A well-documented track record of adherence to security standards provides a level of credibility that can significantly enhance your selling proposition. Additionally, maintaining up-to-date intellectual property protections—like proprietary intrusion detection methods or unique software tools—can further distinguish your business in a crowded market.
Service Lines: Managed vs. Project-Based
Managed Security Services (MSS)
Ongoing partnerships that furnish clients with continuous threat monitoring, SOC (Security Operations Center) management, or cloud security oversight.
Often billed monthly or annually, creating a reliable revenue base that boosts your cybersecurity business valuation by reducing revenue volatility.
Demonstrates the potential for future growth, especially if you can scale managed services to more clients under a standardized framework.
One-Time Assessments (Penetration Testing, Vulnerability Audits)
Clients engage you periodically for specialized tasks like penetration testing, social engineering exercises, or advanced vulnerability audits.
Revenue can fluctuate, and future income is less predictable without contracts to support repeated engagements.
While project-based work still boosts your top line, it likely will not command the same multiple as recurring services when selling a cybersecurity business.
Specialized Solutions (Incident Response, IoT Security, Forensics)
Often require advanced certifications and niche skill sets, leading to higher profit margins.
Can elevate brand differentiation, especially if you have a strong track record in critical incident response or specialized fields like ICS (Industrial Control Systems) or IoT security.
Buyers looking to expand their portfolio or bolster internal capabilities may pay a premium to acquire niche expertise.
| Service Mix | Revenue Stability | Typical Valuation Multiple (Relative) |
|---|---|---|
| Mostly Managed Security Services (MSS) | High | Higher (e.g., 5–6× SDE) |
| Balanced (MSS + Project-Based Contracts) | Moderate | Moderate–Higher (4–5× SDE) |
| Mostly One-Time or Seasonal Assessments | Lower | Lower (3–4× SDE) |
Target Markets: SMB vs. Enterprise vs. Government
SMB Clients
Often rely on outsourced cyber security solutions due to limited in-house capabilities.
May generate smaller individual contracts compared to enterprise clients.
High churn risk if clients graduate to building their own security teams—but a managed services approach can mitigate this by offering scalability and cost-effectiveness.
Enterprise & Government
Typically require stringent compliance and robust service levels, resulting in higher-value contracts.
Longer sales cycles and heavier due diligence processes, but once aboard, enterprise or government clients can be a steady source of revenue.
Can lead to significant brand credibility; having a recognized client portfolio can attract strategic buyers seeking immediate market expansion.
Operational Factors Affecting Valuation
Owner Dependence
If the current owner is the primary architect of security solutions or the main point of client contact, investors may see a heightened risk.
Drafting standard operating procedures (SOPs), training a capable second-tier management team, and developing documented technology roadmaps can reduce dependency on you as the founder.
A smoother transition with minimal owner reliance typically fetches a higher valuation in a cybersecurity business sale.
Skilled Expertise & Tech Tools
Demonstrating a well-trained roster of certified analysts—such as CISSP, CISM, or CEH holders—signals future operational stability.
Proprietary threat models, vulnerability scanning tools, or unique AI-driven security solutions can elevate your competitive edge.
Document these innovations as intellectual property or proprietary methodology for potential buyers to assess quickly.
Compliance & Certifications
Up-to-date alignment with global standards like NIST, ISO 27001, or GDPR underscores the maturity of your operations.
Showcasing robust compliance with industry frameworks increases buyer confidence and helps justify premium valuation multiples.
Maintaining a strong legal and contractual framework—particularly in handling personally identifiable information—minimizes regulatory risk.
Infrastructure & IP
Modern infrastructure (e.g., cloud-based SOC, advanced data analytics platforms) enhances operational efficiency.
Any intellectual property, such as in-house detection algorithms or encryption technologies, represents tangible assets that can raise the perceived worth of your cybersecurity business.
Keep meticulous documentation on how these assets function so potential buyers can quickly understand their revenue-generating potential.
Growth Potential and Industry Trends
Service Expansion
Offering new services—like zero-trust architecture consultancy, extended detection and response (XDR), or niche compliance solutions—can diversify revenue.
As industries like healthcare and manufacturing ramp up security investments, tailoring specialized packages to these verticals can open new revenue streams.
Emphasizing a robust roadmap for expansions or product additions helps prospective buyers envision an immediate path to scaling.
Global Demand for Cybersecurity
The constant evolution of threats (e.g., ransomware, phishing, nation-state hacking) drives global market growth.
Buyers often pay for stable finances plus future upside, so highlight how emerging threats create opportunities for your security services.
Demonstrating that your offerings are well-positioned in an ascendant market can secure a stronger multiple when exiting.
Partnerships & Alliances
Collaborations with cloud providers, software vendors, or managed IT service companies can boost your business’s recurring revenue potential.
Access to new customer networks through integrators or channel partners can reduce customer acquisition cost (CAC) while broadening market presence.
Buyers value established channel partner relationships because they mitigate client pipeline risks and expedite growth.
| Value Driver | Example | Impact on Valuation |
|---|---|---|
| Recurring Revenue | 100+ managed security contracts | +0.5× to 1× multiple |
| Specialized Expertise | Advanced incident response team | Reduces risk, higher multiple |
| Proprietary Technology | Exclusive threat intelligence platform | Increases buyer confidence |
| Growth Opportunities | Potential expansion into IoT security | Justifies premium pricing |
Who’s Buying and Why It Matters
Individual Buyers & Entrepreneurs
Often first-time owners who want a turnkey service business with relatively predictable cash flow.
May rely on seller financing or transitional support, so be prepared with clean documentation and standard operating procedures.
Typically look for stable, recurring contracts and a team in place to run day-to-day operations without constant founder oversight.
Strategic Acquirers (Large Competitors, Complementary Firms)
Specialized cybersecurity businesses that either compete with or complement your offerings may pay a premium to fill a specific service or market gap.
For instance, a large managed IT services firm might acquire your niche threat detection platform to broaden its security portfolio.
Strategic acquirers often have extensive M&A experience and place a high value on synergy, operational efficiency, and expansions to new end markets.
Private Equity & Investment Groups
Are attracted to recurring service models, established brand reputation, and consistent margins.
Typically look for strong leadership, robust systems, and high growth potential to maximize returns within three to seven years.
May allow you to retain partial ownership, providing both an exit and a chance to benefit from continued growth post-acquisition.
Practical Steps to Increase Your Valuation
Maintain Transparent Financial Records:
Adopt GAAP standards for clarity and consistency in your income statements and balance sheets.
Keep personal expenses separate from the company’s finances to reflect a clean seller’s discretionary earnings (SDE) or EBITDA.
Provide up to three years’ worth of financial data to help buyers gauge performance trends.
Strengthen Recurring Revenue:
Convert project-based clients to monthly or annual managed security service contracts whenever possible.
Develop tiered offerings (basic, premium, enterprise) to encourage upsells and align value with cost.
Emphasize stable, long-term engagements that reassure buyers of future cash flow.
Diversify Client Base & Service Portfolio:
Avoid over-reliance on a single client or narrow service line—balance enterprise, SMB, and government opportunities.
Evaluate expansions like penetration testing add-ons, legal e-discovery support, or specialized ICS/SCADA security services to attract new niches.
Present clear vertical-specific solutions (healthcare, finance, retail) that prove your versatility.
Reduce Owner Dependence & Document SOPs:
Cross-train employees to handle key operational and technical tasks.
Develop a digital knowledge base for critical processes like threat intelligence analysis or vulnerability reporting.
If buyers see that day-to-day workflows will continue seamlessly in your absence, they’re more likely to pay a higher valuation.
Highlight Growth & Scalability:
Showcase the potential for geographic expansion, new strategic alliances, or advanced R&D.
Create marketing materials that track lead conversions, client retention, and average revenue per user (ARPU) to paint a compelling growth story.
Illustrate how additional capital injection can propel your cybersecurity firm’s runway, letting buyers envision rapid scaling post-acquisition.
Example Scenario: Two Cyber Security Companies
Company A
Services: 60% managed security services (continuous monitoring, cloud security), 40% project-based penetration testing
Clients: Mix of SMB and mid-market enterprise, with a focus on healthcare compliance
Operations: Documented SOPs for threat intelligence, stable leadership team, automated billing for MSS contracts
Growth: Dedicated R&D unit exploring IoT and AI-driven security tools
Estimated Valuation Multiple: ~5–6× SDE (high stability, advanced tech, diversified client base)
Company B
Services: 80% one-time engagements focused on vulnerability scanning, 20% compliance audits
Clients: Unbalanced base with most revenue coming from a handful of major corporations
Operations: Heavily owner-dependent, minimal process documentation, limited marketing strategy
Growth: No clear plan for recurring revenue expansion or specialized niche services
Estimated Valuation Multiple: ~3–4× SDE (less predictable income, high founder reliance)
Summary
Essential Services & Recurring Revenue: Because cybersecurity protects organizations against ever-evolving threats, offering managed security services can substantially boost your business’s valuation.
Diverse Client Base: Spreading your risk across SMB, enterprise, and government clients helps stabilize income and reduce buyer concerns.
Reduced Owner Dependence: Transitioning critical responsibilities away from the founder, coupled with thorough SOPs, makes your cybersecurity business more marketable.
Growth Potential: Articulating a clear plan for service line expansion, emerging technology adoption, or geographic reach can spur investor interest and command premium pricing.
Buyer Profiles: Different buyers (individuals, strategic acquirers, or private equity) look for various strengths—knowing their motivations helps you tailor your exit approach.
Next Steps
Selling a cybersecurity business involves deep analysis of recurring revenue streams, client relationships, and in-house technical capabilities. By highlighting stable cash flow, compliant operations, and a path to future growth, you can maximize your company’s value in today’s vibrant M&A landscape.
Schedule a free confidential consultation to:
Discuss standard valuation multiples for cybersecurity businesses and how to distinguish yours in a rapidly expanding market.
Receive tailored guidance on improving your exit strategy—from organizing financials to strengthening leadership.
Identify the most attractive buyer types and streamline your path to a successful transition. Yogurt
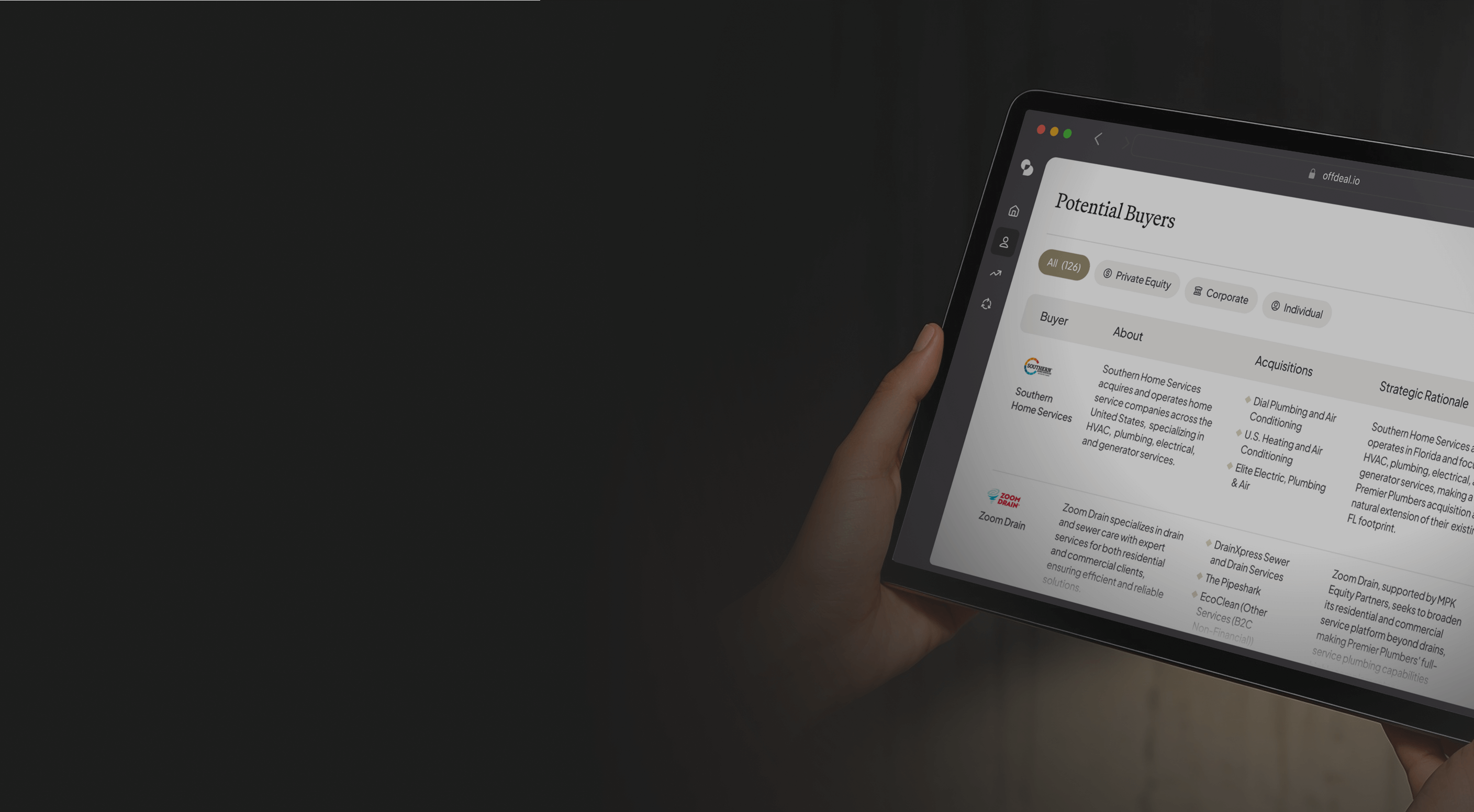
Preview Buyers for Free
Try our buyer match tool to receive a personalized list of active buyers in your industry