Article
December 8, 2024
Building a Digital Data Room: Best Practices for Secure Document Sharing
Future-proof your business with secure data rooms that streamline due diligence and protect data

Table of Contents
For many small business owners, the thought of sharing sensitive information can spark a flurry of concerns: “What if the wrong person sees our financials? What if there’s a data breach right before a critical transaction?” These are valid worries. While email attachments and file-sharing links may have worked in the past, they often fall short of delivering the robust security and organizational clarity you need for important documentation—especially during due diligence, investor pitches, or merger and acquisition talks. That’s why building a digital data room isn’t just a “nice-to-have,” but a pivotal step in ensuring secure document sharing that supports your long-term goals.
Below, we’ll walk you through comprehensive Data Room Best Practices—from selecting the right platform and setting up proper permissions to implementing encryption and version control. By the end of this guide, you’ll understand exactly how to future-proof your document management, earn stakeholder trust, and drive smarter decisions for your company’s growth.
What You’ll Learn
In this in-depth guide, you’ll discover:
How a secure digital data room can help you reduce risk and protect your company's most sensitive documents
Essential user access controls, encryption methods, and process recommendations that strengthen security
The importance of streamlined folder structures and version control to simplify due diligence
Practical steps to implement Data Room Best Practices and ensure seamless collaboration
Strategies to avoid pitfalls, reduce complexity, and maintain professional standards for outside investors and internal teams
Most importantly, you’ll gain the know-how to confidently migrate from ad-hoc file sharing to a robust digital data room designed with small business owners in mind.
Why a Digital Data Room Matters for Small Businesses
For most small business owners, the company itself is the cornerstone asset—often representing a significant portion of personal wealth. A secure digital data room serves as a fortified virtual “vault” for your sensitive records. Whether you’re planning a critical transaction or simply taking proactive steps to safeguard your intellectual property, setting up a digital data room can bring a higher level of professionalism and confidence.
Meeting Increased Demands
As your business grows:
More vendors and partners require up-to-date information.
Employees need remote access without compromising security.
Potential investors, lenders, or M&A advisors will ask for extensive documentation.
A digital data room streamlines these demands by consolidating files in one controlled environment with robust Data Room Best Practices at its core.
Realizing Improved Efficiency and Confidence
Consider how many hours your team spends digging through emails or local folders to find critical documents:
A single missed file can delay deals or prompt extra scrutiny from a buyer.
Disorganized financial records can reduce perceived company value.
By contrast, a meticulously organized data room can:
Save you and your collaborators from frantic last-minute searches.
Instantly signal preparedness to investors or strategic partners.
Safeguard your reputation as a reliable business operator.
Protecting Your Company’s Value
When crucial documents leak or unreliable access controls lead to unauthorized sharing, the fallout can be damaging:
You risk losing trade secrets or competitive advantages.
Regulatory compliance issues may arise, leading to penalties.
Deal negotiations may collapse due to doubts about your operational rigor.
A properly set up digital data room doesn’t just store your files—it’s the gateway to controlled distribution, improved due diligence, and a solid foundation for negotiations, especially when the stakes are high.
Foundational Elements of a Secure Data Room
Managing a secure digital data room means melding layered technical safeguards with well-defined policies. Let’s explore the core building blocks.
Permissions and Role-Based Access Control
One of the most critical aspects of Data Room Best Practices is setting granular permissions. Small business owners often fall into the trap of granting universal access to ease collaboration, but this can backfire if sensitive documents land in the wrong hands.
Key questions to guide permission settings:
How many people should have administrative access to create or delete files?
Should certain documents (like legal or financial records) remain visible only to top-level executives?
Does each department (finance, operations, R&D) need distinct levels of access?
For instance, you might assign “View Only” access to outside advisors or “Edit” access to your internal finance manager.
Below is a quick-reference table to illustrate common roles:
| Role | Access Level |
|---|---|
| Admin | Full create, view, edit, delete rights |
| Manager | Can create folders, upload files, edit user access (if granted) |
| Contributor | Can upload and edit specific files or folders |
| View-Only | Restricted to viewing documents (downloading may be disabled) |
| External Advisor | Typically “View Only” with short-term, time-bound permissions |
Each role can be adjusted in scope, depending on your organizational needs. Proper access control helps minimize risk and preserve confidentiality.
End-to-End Encryption
Encryption acts like a virtual vault your files pass through en route to their destination. Without encryption, data is vulnerable to interception, especially over public networks.
Common forms of encryption:
Transport Layer Security (TLS): Protects data in transit as it moves between the server and user.
At-Rest Encryption: Safeguards documents while they’re stored on your service provider’s servers.
Look for data room platforms that combine both standards, often referred to as “end-to-end encryption.” This ensures that whether files are being uploaded, viewed, or simply sleeping on a server, they remain inaccessible to unauthorized parties.
Multi-Factor Authentication (MFA)
Relying on just passwords creates a single point of failure. Multi-Factor Authentication (MFA) helps mitigate this:
Something you know (password).
Something you have (smartphone or hardware token).
Something you are (biometric scan).
Particularly for administrators and high-level managers, MFA is a must to guard the “keys to the kingdom.” Passwords alone can be compromised in phishing attacks or data breaches; MFA adds that extra shield.
Watermarking and Activity Tracking
If you foresee distributing sensitive content for new partnerships or funding rounds, watermarking each document or page helps you track leaks and maintain accountability.
With robust tracking tools, you can:
See who viewed which documents and at what time.
Detect repeated download attempts that could suggest malicious activity.
Quickly revoke or update access if suspicious behavior occurs.
Implementing Best Practices for Document Sharing
Once your data room is up and running, optimizing it for security and ease of use is the next big step.
Organizing Files for Clarity
Imagine someone visiting your data room for the first time. Do they see a cluttered mess or a streamlined folder structure that guides them naturally? Organizing documents isn’t just good housekeeping—it’s crucial for an efficient due diligence process and daily operations.
A well-structured data room might look like this:
Such categorization helps:
Potential investors or collaborators navigate efficiently.
Prevent confusion between older and newer versions of the same file.
Keep relevant documents together for each major area of your business.
Version Control and Check-In/Check-Out
Version confusion can derail negotiations and hamper internal projects.
Best Practices for version control include:
Labeling each significant update with a clear version number: (v1.0, v2.1, etc.).
Employing “check-in/check-out” so only one person can edit a document at a time.
Keeping a change log or revision history for accountability.
With a robust version control system, you won’t waste time reconciling contradictory edits or verifying which set of financial statements is current.
Secure Sharing Protocols
Whenever collaborating with external parties—investors, auditors, or new partners—consider the protocols you use to grant them data room access:
Limited, time-bound invitations that expire after a set date.
Automatic NDAs that pop up for acceptance before viewing.
Watermarked documents that include an identifier such as the viewer’s username or email address.
By layering these controls on top of encryption and role-based permissions, you reduce the chance that outsiders can download, screenshot, or redistribute documents without your knowledge.
Common Mistakes to Avoid
Even the best systems fail under user error or oversight. Steer clear of these pitfalls:
Giving everyone the same level of access for convenience
Storing old or irrelevant documents “just in case”
Neglecting to regularly test your data recovery process
Assuming strong passwords alone suffice for security
Overlooking the need for quick user deactivation when an employee leaves the company
Each misstep can open a window for data leaks, confusion, or unauthorized access—so consistent oversight is paramount.
Maintaining and Monitoring for Ongoing Security
Building a digital data room is a solid start, but it’s not a “set it and forget it” initiative. To align with industry-level Data Room Best Practices, continuous monitoring and updates are critical.
Regular Audits and Access Reviews
At minimum, small business owners should conduct quarterly or biannual audits of data room access:
Review active users to ensure their permissions align with current roles.
Check for dormant accounts that can be removed or disabled.
Verify that no unauthorized folders or files have appeared.
One-time diligence isn’t enough. A scheduled review helps you maintain the integrity and relevance of the data room while ensuring only the right people have authority to see or modify sensitive content.
Updating Security Protocols
Threats evolve, and so does technology. Keep your data room aligned with emerging Data Room Best Practices by:
Upgrading to newer encryption standards when advised by your provider.
Turning on advanced logging or analytics features offered in new software updates.
Revisiting how you label and categorize sensitive files in response to new regulations or internal policy changes.
Disaster Recovery and Backups
No digital data room is immune to unexpected server outages or software glitches. Here’s how you can mitigate disruption:
Maintain redundant copies of crucial documents, ideally in geographically dispersed data centers if your provider supports that.
Periodically confirm that backups are valid and recoverable.
Document a disaster recovery plan, outlining who to contact and the steps to follow in a worst-case scenario.
Having a fail-safe ensures that if your primary data room goes down at a critical moment—like during M&A negotiations—you can swiftly restore operations.
Conclusion: Protecting Your Business with a Secure Digital Data Room
Building a secure digital data room is about more than just locking away your documents—it’s about operating from a stance of preparedness, professionalism, and resilience. By adhering to rigorous Data Room Best Practices, your small business can confidently engage with clients, investors, auditors, and potential buyers.
Key Takeaways
A well-organized data room boosts efficiency, fosters trust, and streamlines diligence processes.
Role-based permissions, encryption, and MFA form a protective trifecta.
Watermarking and version control add a layer of accountability critical for external reviews.
Ongoing monitoring—through regular audits and security updates—keeps your data room viable and safe.
Next Steps
Whether you’re preparing for a funding round, an exit strategy, or you simply want to safeguard your company’s valuable data, setting up a digital data room should top your priority list. Proactive planning today can spare you from vulnerabilities tomorrow.
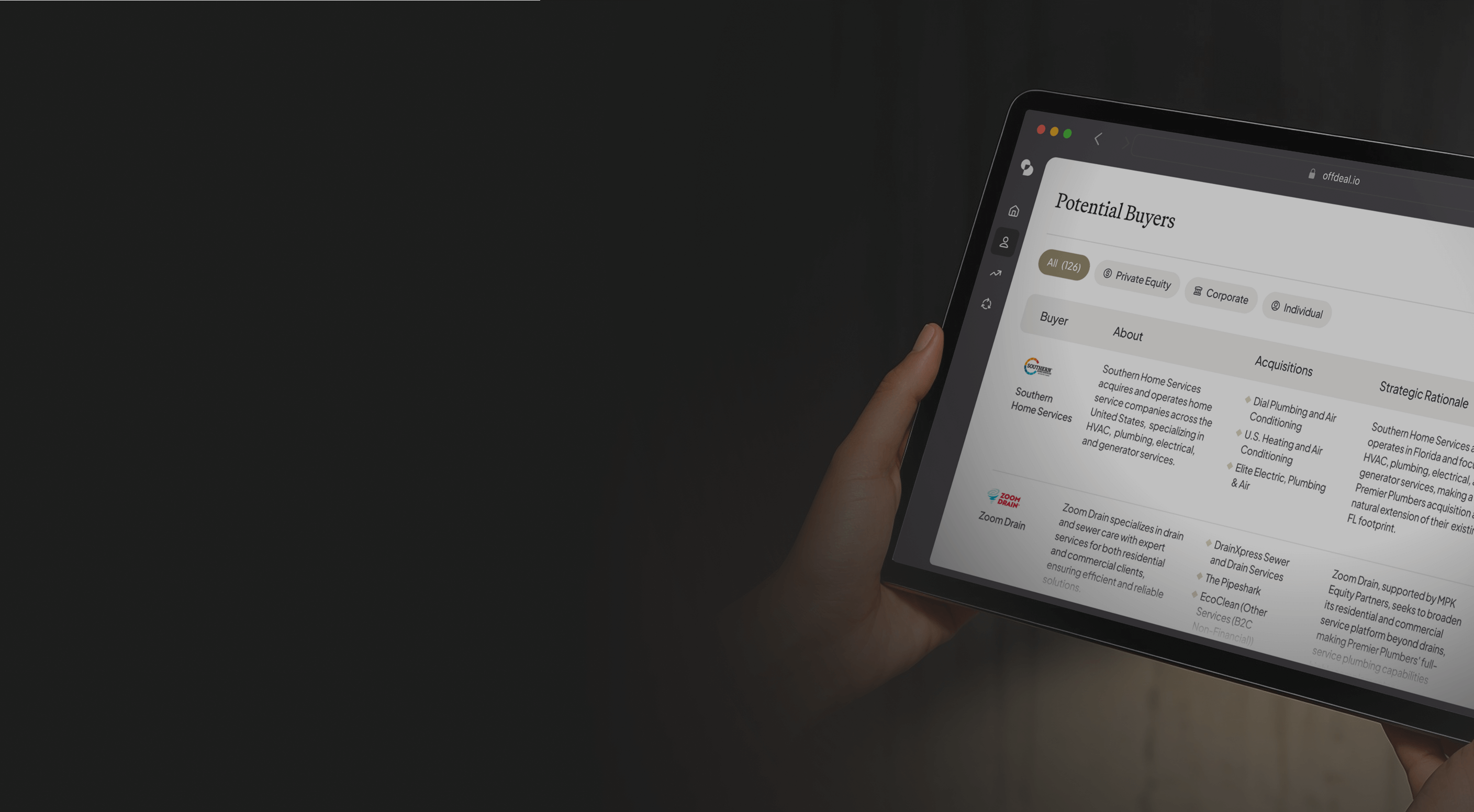
Preview Buyers for Free
Try our buyer match tool to receive a personalized list of active buyers in your industry